Gutter Cat Gang Hack Results In $700,000+ of Lost NFTs
2 comments

In the digital realm of cryptocurrencies and blockchain technology, security is of paramount importance. Unfortunately, even well-known projects like Gutter Cat Gang (GCG) are not immune to cyberattacks. Recently, the GCG official Twitter accounts were compromised in a reported SIM swap attack that resulted in the draining of unsuspecting users wallets. This article delves into the details of the incident, explores the concept of a SIM swap attack, and emphasizes the significance of robust cybersecurity practices to protect valuable assets in the crypto space.
The Gutter Cat Gang Incident
On July 7, at approximately 8 pm UTC, Gutter Cat Gang co-founder @GutterMitch alerted followers that their Twitter account had been compromised. They cautioned against interacting with any links shared from their compromised account. Additionally, the Twitter account of co-founder @gutteric was also hacked. The attackers used these accounts to impersonate GCG tweets, offering links to fake "limited edition" Gutter Cat Gang NFT sneaker airdrops. Regrettably, individuals who clicked on these links unknowingly had their hot wallets drained, resulting in substantial losses.
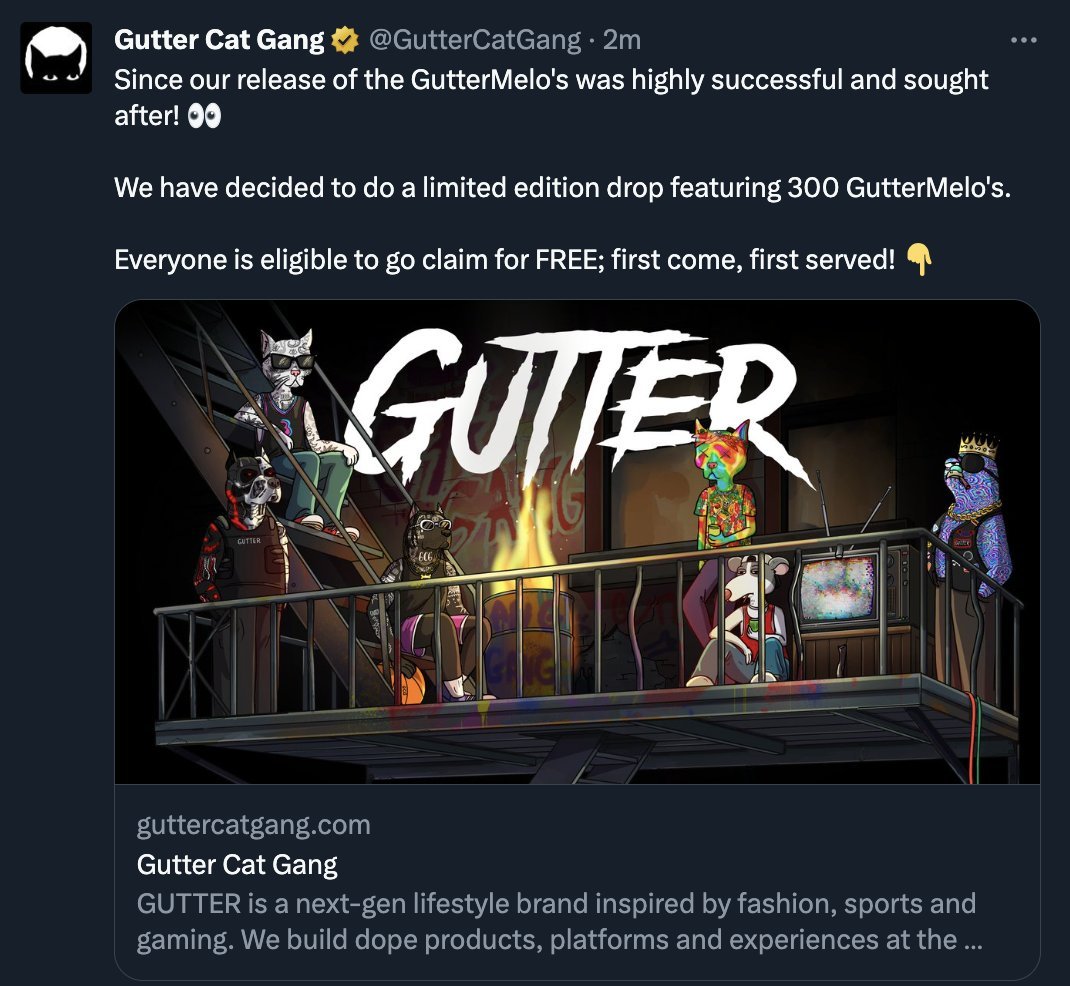
The SIM Swap Attack
According to prominent blockchain sleuth ZachXBT, the Gutter Cat Gang team likely fell victim to a SIM swap attack. This type of cyberattack involves hackers exploiting security vulnerabilities in mobile phone service providers' systems to gain control of a victim's phone number. By impersonating the victim, the attackers can intercept SMS-based two-factor authentication (2FA) codes and gain unauthorized access to sensitive accounts, such as social media profiles or cryptocurrency wallets.
The Consequences and Lessons Learned
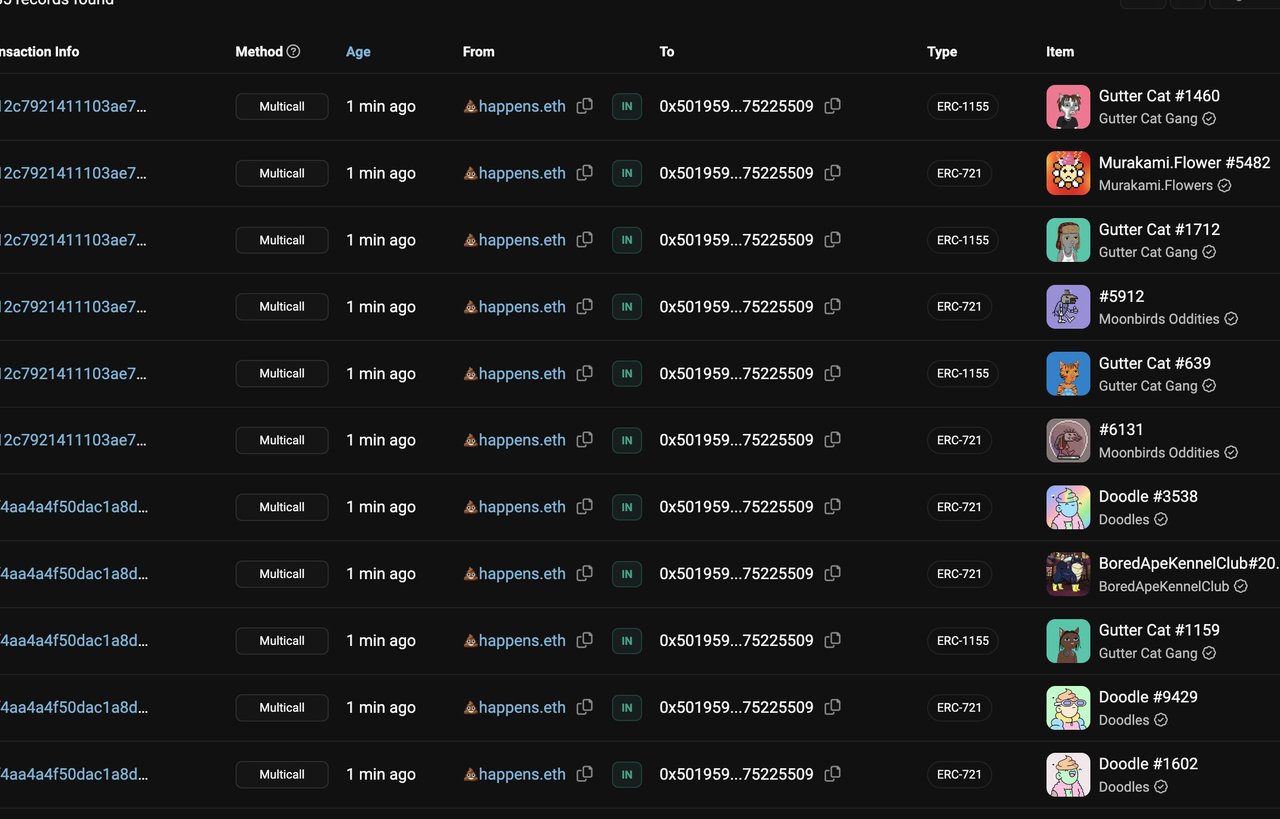
The consequences of the Gutter Cat Gang SIM swap attack were devastating for some victims. ZachXBT highlighted two individuals who suffered significant losses. One lost a Bored Ape Yacht Club NFT valued at approximately $65,913, while another (reported to be crypto influencer doge4doge) lost an astonishing $700,000 worth of NFTs from various prominent collections. These incidents underscore the need for increased awareness about the potential risks in the crypto space and the importance of implementing robust security measures, including adopting more secure forms of 2FA and avoiding reliance solely on SMS-based verification.
Strengthening Cybersecurity Practices
To safeguard valuable digital assets, crypto enthusiasts must prioritize cybersecurity practices. First and foremost, it is essential to avoid using SMS-based 2FA for accounts related to cryptocurrencies or other sensitive platforms. Instead, opt for more secure alternatives such as hardware wallets or authenticator apps that generate time-based one-time passwords (TOTPs). Additionally, regularly review and update passwords, enable multi-factor authentication wherever possible, and stay informed about the latest security threats and best practices in the crypto community.
Community Support and Compensation
In the aftermath of the Gutter Cat Gang incident, the affected individuals deserve support and compensation. It is incumbent upon the GCG team to address the situation responsibly and consider a compensation plan for the victims. Such actions not only demonstrate accountability but also contribute to building trust within the crypto community and promoting a safer environment for all participants.
Conclusion
The SIM swap attack on Gutter Cat Gang serves as a stark reminder of the ever-present cybersecurity risks in the crypto world. Protecting your digital assets requires constant vigilance and proactive measures. By adopting robust security practices, such as implementing strong authentication methods and staying informed about emerging threats, you can reduce the risk of falling victim to malicious attacks. Let this incident serve as a call to action for the crypto community to prioritize security and protect the integrity of this transformative technology.
Comments